| Line 1: | Line 1: | ||
| − | == |
+ | == Definitions == |
| + | === General === |
||
| ⚫ | |||
| + | |||
| ⚫ | |||
{{Quote|[a]n approach used to plan, design, develop, [[test]], and [[implement]] an [[application system]] or a major [[modification]] to an [[application system]].<ref>[[FFIEC IT Examination Handbook]], Audit, Appendix B: Glossary ([http://ithandbook.ffiec.gov/it-booklets/audit/appendix-b-glossary.aspx full-text]).</ref>}} |
{{Quote|[a]n approach used to plan, design, develop, [[test]], and [[implement]] an [[application system]] or a major [[modification]] to an [[application system]].<ref>[[FFIEC IT Examination Handbook]], Audit, Appendix B: Glossary ([http://ithandbook.ffiec.gov/it-booklets/audit/appendix-b-glossary.aspx full-text]).</ref>}} |
||
{{Quote|[t]he scope of activities associated with a [[system]], encompassing the [[system]]'s initiation, [[system development|development]] and [[acquisition]], [[implementation]], operation and [[maintenance]], and ultimately its [[disposal]].<ref>[[CNSSI 4009]].</ref>}} |
{{Quote|[t]he scope of activities associated with a [[system]], encompassing the [[system]]'s initiation, [[system development|development]] and [[acquisition]], [[implementation]], operation and [[maintenance]], and ultimately its [[disposal]].<ref>[[CNSSI 4009]].</ref>}} |
||
| + | |||
| + | === Software === |
||
| + | |||
| + | A '''System[s] Development Life Cycle''' ('''SDLC''') is |
||
| + | |||
| + | {{Quote|a series of prescribed [[procedure]]s or steps for the rational and timely development, operational use, and [[maintenance]] of [[computer software]]. The procedures define the sequence in which analysis, design, [[coding]] and [[testing]] methods are applied, the tools used to support those methods, the [[deliverable]]s that are required, the controls to assure quality and coordinate change and the [[milestone]]s that enable assessment of progress. Variations in selection of a particular life cycle are influenced by the scope and complexity of projects or applications, the methods and tools to be used, and the controls and [[deliverable]]s required.<ref>Michigan Dept. of Tech., Management & Budget, 8000 Glossary (Jan. 6, 1997) ([http://www.michigan.gov/dmb/0,4568,7-150-9131_9347-29688--,00.html#C full-text]).</ref>}} |
||
== Overview == |
== Overview == |
||
Revision as of 03:50, 17 August 2012
Definitions
General
A System[s] Development Life Cycle (SDLC) is
| “ | [a]n approach used to plan, design, develop, test, and implement an application system or a major modification to an application system.[1] | ” |
| “ | [t]he scope of activities associated with a system, encompassing the system's initiation, development and acquisition, implementation, operation and maintenance, and ultimately its disposal.[2] | ” |
Software
A System[s] Development Life Cycle (SDLC) is
| “ | a series of prescribed procedures or steps for the rational and timely development, operational use, and maintenance of computer software. The procedures define the sequence in which analysis, design, coding and testing methods are applied, the tools used to support those methods, the deliverables that are required, the controls to assure quality and coordinate change and the milestones that enable assessment of progress. Variations in selection of a particular life cycle are influenced by the scope and complexity of projects or applications, the methods and tools to be used, and the controls and deliverables required.[3] | ” |
Overview
There are eight distinct phases in the SDLC as depicted in the figure below:
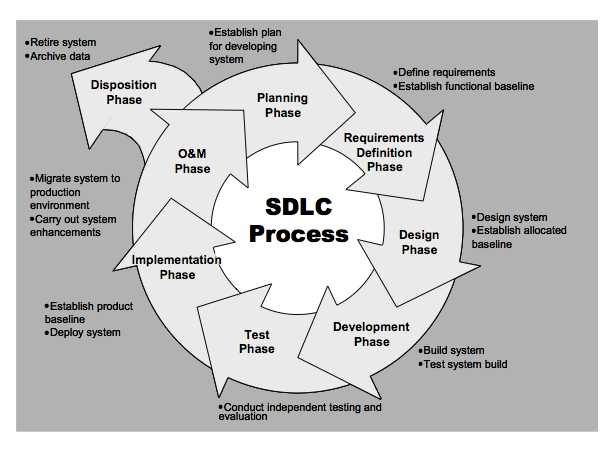
SDLC Process
Throughout the System Development Life Cycle system owners must be cognizant of changes to the system. Since systems routinely experience changes over time to accommodate new requirements, new technologies or new risks, they must be routinely analyzed in respect to the security posture. Minor changes typically have little impact to the security posture of a system. These changes can be standard maintenance, adding or deleting users, applying standard security patches, or other routine activities. However, significant changes require an added level of attention and action. Changes, such as installing a new operating system, port modification, new hardware platforms, or changes to the security controls should trigger a re-authorization of the system
References
- ↑ FFIEC IT Examination Handbook, Audit, Appendix B: Glossary (full-text).
- ↑ CNSSI 4009.
- ↑ Michigan Dept. of Tech., Management & Budget, 8000 Glossary (Jan. 6, 1997) (full-text).