Definition[]
The Identity Ecosystem is an online environment where individuals, organizations, services, and devices can trust each other because authoritative sources establish and authenticate their digital identities.
Overview[]
The Identity Ecosystem enables:
- Security, by making it more difficult for adversaries to compromise online transactions;
- Efficiency based on convenience for individuals who may choose to manage fewer passwords or accounts than they do today, and for the private sector, which stands to benefit from a reduction in paper-based and account management processes;
- Ease-of-use by automating identity solutions whenever possible and basing them on technology that is easy to operate with minimal training;
- Confidence that digital identities are adequately protected, thereby increasing the use of the Internet for various types of online transactions;
- Increased privacy for individuals, who rely on their data being handled responsibly and who are routinely informed about those who are collecting their data and the purposes for which it is being used;
- Greater choice, as identity credentials and devices are offered by providers using interoperable platforms; and
- Opportunities for innovation, as service providers develop or expand the services offered online, particularly those services that are inherently higher in risk.
Ecosystem components[]
The Identity Ecosystem is composed of three layers:
- Execution layer – conducts transactions in accordance with the rules of the Identity Ecosystem.
- Management layer – applies and enforces the rules for participants in the Identity Ecosystem.
- Governance layer – Establishes the rules required to function within the Identity Ecosystem.
The layers of the Identity Ecosystem identify the participants, policies, processes, and technologies required to provide trusted identification, authentication, and authorization across diverse transaction types.
Listed below are the various participants in the Identity Ecosystem. It is important to note that a single organization need not fill each discrete role; rather, it is possible that an organization provides services that cross multiple roles.
- An individual is the person engaged in an online transaction. A digital identity, which is a set of attributes, represents an individual in a transaction.
- A non-person entity (NPE) may require authentication in the Identity Ecosystem. NPEs can be an organizations, hardware, software, or services and are treated much like individuals within the Identity Ecosystem. NPEs may engage in a transaction or simply support it.
- Individuals and NPEs are collectively referred to as the subjects of a transaction.
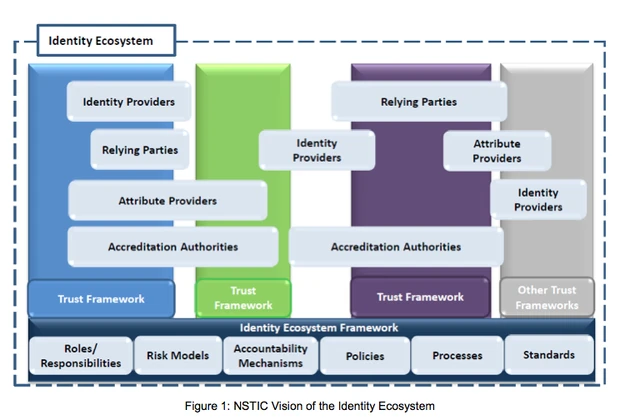
- An Identity provider (IDP) is responsible for the processes associated with enrolling a subject, and establishing and maintaining the digital identity associated with an individual or NPE. These processes include identity vetting and proofing, as well as revocation, suspension, and recovery of the digital identity. The IDP is responsible for issuing a credential, the information object or device used during a transaction to provide evidence of the subject’s identity; it may also provide linkage to authority, roles, rights, privileges, and other attributes.
- The credential can be stored on an identity medium, which is a device or object (physical or virtual) used for storing one or more credentials, claims, or attributes related to a subject. Identity media are widely available in many formats, such as smart cards, security chips embedded in PCs, cell phones, software-based certificates, and USB devices. Selection of the appropriate credential is implementation specific and dependent on the risk tolerance of the participating entities.
- An Attribute Provider (AP) is responsible for the processes associated with establishing and maintaining identity attributes. Attribute maintenance includes validation, updates, and revocation. Attributes are a named quality or characteristic inherent or ascribed to someone or something (e.g., "Jane’s age is at least 21 years"). An attribute provider asserts trusted and validated attribute claims in response to attribute requests from relying parties. In certain instances, a subject may self-assert attribute claims to relying parties; however, relying parties often depend upon attribute assertions from trusted third parties capable of validating the accuracy of claims. Trusted, validated attributes form the basis by which relying parties will authorize subjects.
- A Relying Party (RP) makes transaction decisions based upon its receipt, validation, and acceptance of a subject's authenticated credentials and attributes. Within the Identity Ecosystem, a relying party selects and trusts identity, credential, and attribute providers of their choice based on risk and functional requirements. Relying parties are not required to integrate with all permutations of identity media. Rather, they will trust an identity provider's assertion of a valid subject credential as appropriate. Relying parties also typically need to identify and authenticate themselves to the subject as part of transactions in the Identity Ecosystem.
- Participants refer to the collective subjects, relying parties, identity media, service providers, and NPEs within a given transaction.
- A Trustmark is a badge, seal, image or logo that indicates a product or service provider has met the requirements of the Identity Ecosystem, as determined by an accreditation authority. To maintain trustmark integrity, the trustmark itself must be resistant to tampering and forgery; participants should be able to both visually and electronically validate its authenticity. The trustmark provides a visible symbol to serve as an aid for individuals and organizations to make informed choices about the providers and identity media they use.
- The Identity Ecosystem Framework is the overarching set of interoperability standards, risk models, privacy and liability policies, trustmark requirements, and enforcement mechanisms that govern the Identity Ecosystem.
- A Governance Authority oversees and maintains the Identity Ecosystem Framework and defines the rules by which a product or service provider in the Identity Ecosystem attains trustmarks. In addition, the Governance Authority is accountable for certifying organizations that wish to become Accreditation Authorities.
- An Accreditation Authority assesses and validates that identity providers, attribute providers, relying parties, and identity media adhere to an agreed upon Trust Framework.
- A Trust Framework defines the rights and responsibilities of a particular set of participants in the Identity Ecosystem; specifies the rules that govern their participation; and outlines the processes and procedures that provide assurance. A Trust Framework considers the level of risk associated with a given transaction and its participants. Many different Trust Frameworks can exist within the Identity Ecosystem, as sets of participants can tailor them to their particular needs. However, the participants must align the Trust Frameworks with the overall Identity Ecosystem Framework.
Privacy protection and voluntary participation[]
Privacy protection and voluntary participation are pillars of the Identity Ecosystem. The Identity Ecosystem protects anonymous parties by keeping their identity a secret and sharing only the information necessary to complete the transaction. For example, the Identity Ecosystem allows an individual to provide age without releasing birth date, name, address, or other personally identifying data. At the other end of the spectrum, the Identity Ecosystem supports transactions that require high assurance of a participant’s identity. The Identity Ecosystem reduces the risk of exploitation of information by unauthorized access through more robust access control techniques. Finally, participation in the Identity Ecosystem should be voluntary for both organizations and individuals.
Identity solutions should preserve the positive privacy benefits of offline transactions, while mitigating some of the negative privacy aspects. The eight Fair Information Practice Principles (FIPPs) — Transparency, Individual Participation, Purpose Specification, Data Minimization, Use Limitation, Data Quality and Integrity, Security, and Accountability and Auditing — are the widely accepted framework for evaluating and mitigating privacy impacts.
Universal and integrated adoption of the FIPPs in the Identity Ecosystem should enable individuals to understand and make meaningful choices about the use of their personal information in cyberspace. Adoption of the FIPPs should also ensure that organizations limit data collection, only use and distribute personal information that is relevant and necessary, maintain appropriate safeguards on that information, and are responsive and accountable to individuals’ privacy expectations. Fully integrating all of the FIPPs into the Identity Ecosystem will be the key to achieving trusted identities in cyberspace that are truly privacy-enhancing.
Interoperability[]
Another pillar of the Identity Ecosystem is interoperability. The Identity Ecosystem leverages strong and interoperable technologies and processes to enable the appropriate level of trust across participants. Interoperability supports identity portability and enables service providers within the Identity Ecosystem to accept a variety of credential and identification media types. The Identity Ecosystem does not rely on the government to be the sole identity provider. Instead, interoperability enables a variety of public and private sector identity providers to participate in the Identity Ecosystem.
User-centricity[]
Interoperability and privacy protection combine to create a user-centric Identity Ecosystem. User-centricity will allow individuals to select the interoperable credential appropriate for the transaction. Through the creation and adoption of privacy-enhancing policies and standards, individuals will have the ability to transmit no more than the amount of information necessary for the transaction, unless they choose otherwise.
In addition, such standards will inhibit the linking of an individual’s transactions and credential use by service providers. Individuals will have more confidence that they exchange information with the appropriate parties, securely transmit that information, and have the information protected in accordance with privacy best practices.
Source[]
- The White House, (DRAFT) National Strategy for Trusted Identities in Cyberspace 1-2 (June 25, 2010).