Citation[]
Health Information Technology for Economic and Clinical Health (HITECH) Act, Title XIII of Division A and Title IV of Division B of the American Recovery and Reinvestment Act of 2009 (ARRA), Pub. L. No. 111-5, 123 Stat. 226 (Feb. 17, 2009) (full-text), codified at 42 U.S.C. §§300jj et seq.; §§17901 et seq.
Overview[]
The Act, enacted as part of the American Recovery and Reinvestment Act of 2009, allocated billions of dollars for the health care system to adopt and meaningfully use health IT to improve health. It is designed to promote the widespread adoption and standardization of health information technology, and requires the Department of Health and Human Services (HHS) to modify the HIPAA Privacy, Security, and Enforcement Rules to strengthen the privacy and security protections for health information and to improve the workability and effectiveness of the HIPAA Rules.
Section 13402 of the Act requires the Department of Health and Human Services (HHS) to issue interim final regulations within 180 days of enactment to require covered entities under the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and their business associates to provide for notification in the case of breaches of unsecured protected health information.
Further, the Act provides that no later than 60 days after enactment, the Secretary of Health and Human Services shall, after consultation with stakeholders, issue (and annually update) guidance specifying the technologies and methodologies that render PHI unusable, unreadable, or indecipherable to unauthorized individuals.[1]
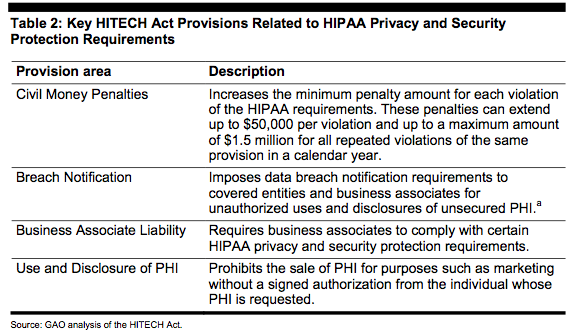
Table 2 below provides a brief overview of the HITECH Act's key provisions for strengthening HIPAA privacy and security protection requirements.
Electronic health records[]
The Act authorized expenditures of at least $20 billion to promote the adoption and use of EHR technologies that would ideally be connected through a national health information network. Hospitals and physicians who make “meaningful use” of interoperable EHRs can qualify for extra payments through Medicare and Medicaid.
Responsibility for developing policies that implement the overall HITECH Act lies primarily with the Office of the National Coordinator for Health Information Technology (ONC). In this role, ONC works closely with the Centers for Medicare and Medicaid Services (CMS), which is responsible for promulgating policies that relate to Medicare and Medicaid payment for meaningful use of EHRs under the HITECH Act. ONC and CMS recently released final rules to implement the first phase of the HITECH Act, which begins in 2011.
The ONC rule specifies the standards, implementation specifications and other criteria for EHR systems and technologies to be certified under the HITECH Act and thus eligible for the Act's incentive programs while the CMS rule specifies how hospitals, physicians, and other eligible professionals must demonstrate their meaningful use of these technologies in order to receive Medicare and Medicaid payment incentives. Both sets of rules strongly indicate that standards and criteria for achieving meaningful use of EHRs will grow more rigorous in subsequent phases (2013 and 2015) as the technology continues to evolve and providers gain experience and sophistication in its use.
Definition of "Breach"[]
(1) BREACH.
(A) IN GENERAL. The term breach means the unauthorized acquisition, access, use, or disclosure of protected health information which compromises the security or privacy of such information, except where an unauthorized person to whom such information is disclosed would not reasonably have been able to retain such information.
(B) EXCEPTIONS. The term breach does not include —
- (i) any unintentional acquisition, access, or use of protected health information by an employee or individual acting under the authority of a covered entity or business associate if —
- (I) such acquisition, access, or use was made in good faith and within the course and scope of the employment or other professional relationship of such employee or individual, respectively, with the covered entity or business associate; and
- (II) such information is not further acquired, accessed, used, or disclosed by any person; or
- (ii) any inadvertent disclosure from an individual who is otherwise authorized to access protected health information at a facility operated by a covered entity or business associate to another similarly situated individual at same facility; and
- (iii) any such information received as a result of such disclosure is not further acquired, accessed, used, or disclosed without authorization by any person.[2]
Privacy[]
Subtitle D of the HITECH Act, entitled “Privacy,” among other provisions, requires the Department of Health and Human Services to issue interim final regulations for breach notification by entities subject to the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and their business associates. In particular, section 13402 of the Act requires HIPAA covered entities to notify affected individuals, and requires business associates to notify covered entities, following the discovery of a breach of unsecured protected health information.
Further, the Act provides that no later than 60 days after enactment, the Secretary shall, after consultation with stakeholders, issue (and annually update) guidance specifying the technologies and methodologies that render protected health information (PHI) unusable, unreadable, or indecipherable to unauthorized individuals.[3]
If PHI is rendered unusable, unreadable, or indecipherable to unauthorized individuals by one or more of the methods identified by the HHS, then such information is not "unsecured" PHI.
Under the Act, state attorneys general can investigate and take action against organizations for failing to secure PHI.
Business associates' civil and criminal liability[]
The HITECH Act provides that covered entities' business associates that obtain or create PHI pursuant to a business associate agreement may only use or disclose that PHI in compliance with its terms.[4] The Act also requires existing business associate agreements to incorporate the new privacy provisions.[5]
Prior to the HITECH Act, covered entities had been liable for violations of the Privacy Rule that were committed by their business associates, but only if the covered entity had knowledge of "a pattern of activity or practice" of the business associate that violates the Privacy Rule.[6] Under the HITECH Act, business associates are also made liable for violations of the Privacy Rule committed by the covered entities with which they contract, if the business associates are aware of a pattern and practice of unlawful conduct by the covered entity.[7] While business associates are still not defined as covered entities under HIPAA, they are subject to the same civil and criminal penalties for improper uses or disclosures of PHI.[8]
The HITECH Act also extended application of the HIPAA Security Rule's provisions on security safeguards and documentation to business associates of covered entities, making those business associates subject to civil and criminal liability for violations of the HIPAA Security Rule.[9] Under the HIPAA Security Rule, only covered entities can be held civilly or criminally liable for violations. While business associates are still not considered covered entities under HIPAA, they are subject to the same civil and criminal penalties as a covered entity for Security Rule violations.[10] The HITECH Act also requires existing business associate agreements to incorporate the new security requirements.[11]
Unsecured protected health information[]
The HITECH Act required the HHS Secretary to issue guidance specifying the technologies and methodologies to render protected health information unusable, unreadable, or indecipherable to unauthorized individuals.[12] The HITECH Act also provides a definition.[13]
Guidance on the meaning of "unsecured protected health information" was issued by HHS that became effective upon issuance. It identified two methods for rendering PHI unusable, unreadable, or indecipherable: encryption and destruction (paper and electronic form). Pursuant to this guidance, "if PHI is rendered unusable, unreadable, or indecipherable to unauthorized individuals by one or more of the methods identified in this guidance, then such information is not 'unsecured' PHI." Because the HITECH Act's breach notification requirements apply only to breaches of unsecured PHI, this guidance provides the means by which covered entities and their business associates can determine whether a breach has occurred and whether notification obligations apply.89
Breach notification[]
The HITECH Act imposed breach notification requirements on covered entities, their business associates, and vendors of personal health records (PHRs).90 The Act requires covered entities, business associates, and vendors of PHRs to notify affected individuals in the event of a "breach" of "unsecured protected health information."91
In August 2009, the HHS issued an interim final breach notification regulation.95 The Breach Notification Interim Final Regulation addresses notification to individuals, the media, and the Secretary, by a business associate; law enforcement delay; and administrative requirements and burdens of proof.
The HITECH Act also directed the Federal Trade Commission (FTC) to issue breach notification regulations for web-based businesses to notify consumers when the security of their electronic personal health information is breached.96 The FTC rule applies to both vendors of personal health records — which provide online repositories that people can use to keep track of their health information — and entities that offer third-party applications for personal health records. It applies to breaches by vendors of PHRs, PHR-related entities, and third-party service providers that [[maintain information on U.S. citizens or residents.97 The rule contains provisions discussing timeliness, methods of notification, content, and enforcement of the breach notification requirements.
Notice of unauthorized disclosure of protected health information[]
The HITECH Act requires a covered entity to notify affected individuals when it discovers that their unsecured PHI has been, or is reasonably believed to have been, breached.98 This requirement applies to covered entities that access, maintain, retain, modify, record, store, destroy, or otherwise hold, use, or disclose unsecured protected health information. The scope of notification is dependant upon the number of individuals whose unsecured PHI was compromised. Generally, only written notice need be provided if less than 500 individuals are involved. For larger breaches, notice through prominent media outlets may be required. In all cases, the Secretary of HHS must be notified, although breaches involving less than 500 people may be reported on an annual basis. The Secretary of HHS is directed to display on the department’s website a list of covered entities with breaches involving more than 500 individuals.99
Generally, notice must be given without unreasonable delay, but no later than 60 days after the breach is discovered. If a delay is not reasonable, a covered entity may still have violated this provision even if notice was given within 60 days. In an enforcement action of this provision, the covered entity has the burden of proving that any delay was reasonable. Delayed notification is permitted for law enforcement purposes if a law enforcement official determines that notice would impede a criminal investigation or cause damage to national security.
To the extent possible, notification of a breach must include a description of what occurred; the types of information involved in the breach; steps individuals should take in response to the breach; what the covered entity is doing to investigate, mitigate, and protect against further harm; and contact information to obtain additional information.
Annually, the Secretary is required to submit a report to Congress containing information on the number and nature of breaches for which notice was provided and actions taken in response to such breaches.100
Notice of unauthorized disclosure of personal health records[]
The HITECH Act includes a breach notification requirement for PHR vendors (such as Google Health or Microsoft Vault), service providers to PHR vendors, and PHR servicers that are not covered entities or business associates that sunsets “if Congress enacts new legislation.”101 Under this breach notification requirement, these entities are required to notify citizens and residents of the United States whose unsecured “PHR identifiable health information” has been, or is believed to have been, breached. PHR vendors, service providers to PHR vendors, and PHR servicers are also required to notify the Federal Trade Commission (FTC).102
The HITECH Act defines several terms specific to the PHR breach notification requirement. A “breach of security” is defined as the unauthorized acquisition of an individual’s PHR identifiable health information.103 PHR identifiable health information is defined as individually identifiable health information, and includes information provided by or on behalf of the individual, and information that can reasonably be used to identify the individual.104
The requirements regarding the scope, timing, and content of these notifications are identical to the requirements applicable to breaches of unsecured PHI. Violations of these requirements shall be considered unfair and deceptive trade practices in violation of the Federal Trade Commission Act.
References[]
- ↑ The Act provides that the technologies and methodologies specified in the guidance also are to address the use of standards developed under section 3002(b)(2)(B)(vi) of the Public Health Service Act, as added by section 13101 of the Act. Section 3002(b)(2)(B)(vi) of the Public Health Service Act requires the HIT Policy Committee established in section 3002 to issue recommendations on the development of technologies that allow individually identifiable health information to be rendered unusable, unreadable, or indecipherable to unauthorized individuals when such information is transmitted in the nationwide health information network or physically transported outside of the secured physical perimeter of a health care provider, health plan, or health care clearinghouse. The Department intends to address such standards as they are developed in future iterations of this guidance.
- ↑ Pub. L. No 111-5, §13400.
- ↑ The Act provides that the technologies and methodologies specified in the guidance also are to address the use of standards developed under section 3002(b)(2)(B)(vi) of the Public Health Service Act, as added by section 13101 of the Act. Section 3002(b)(2)(B)(vi) of the Public Health Service Act requires the HIT Policy Committee established in section 3002 to issue recommendations on the development of technologies that allow individually identifiable health information to be rendered unusable, unreadable, or indecipherable to unauthorized individuals when such information is transmitted in the nationwide health information network or physically transported outside of the secured physical perimeter of a health care provider, health plan, or health care clearinghouse. The [HHS]] intends to address such standards as they are developed in future iterations of this guidance.
- ↑ Id. §13401(c).
- ↑ Id. §13404(a).
- ↑ 45 C.F.R. §164.504(e)(1)(ii).
- ↑ Pub. L. No. 111-5, §13404(b).
- ↑ Id. §§13401(b), 13404(c).
- ↑ Id. §13401. The HITECH Act adopts the same definition of business associates as the HIPAA Privacy and Security Rules. 45 C.F.R. §160.103.
- ↑ Pub. L. No. 111-5, §§13401(b), 13404(c).
- ↑ Id. §13404(a).
- ↑ Id. §13402(h).
- ↑ Under the default definition, PHI is unsecured if "it is not secured by a technology standard that renders protected health information unusable, unreadable, or indecipherable to unauthorized individuals and that is developed or endorsed by a standards developing organization that is accredited by the American National Standards Institute."
Source[]
- Data Security Breach Notification Laws, at 14-17.