Definitions[]
Australia[]
The term cybercrime describes both:
| “ |
|
” |
European Union[]
The term cyber crime
| “ | is applied to three categories of criminal activities. The first covers traditional forms of crime such as fraud or forgery, though in a cyber crime context relates specifically to crimes committed over electronic communication networks and information systems. . . . The second concerns the publication of illegal content over electronic media (i.e. child sexual abuse material or incitement to racial hatred). The third includes crimes unique to electronic networks, i.e. attacks against information systems, denial of service and hacking. These types of attacks can also be directed against the crucial critical infrastructures in Europe and affect existing rapid alert systems in many areas, with potentially disastrous consequences for the whole society. Common to each category of crime is that they may be committed on a mass-scale and with a great geographical distance between the criminal act and its effects. Consequently the technical aspects of applied investigative methods are often the same.[2] | ” |
General[]
Cybercrime "means conduct, with respect to cyber systems. . . ."[3]
Cybercrime is
| “ | [is] criminal activities that specifically target a computer or network for damage or infiltration and also refers to the use of computers as tools to conduct criminal activity.[4] | ” |
United Kingdom[]
Cyber crime is
| “ | cyber-dependent crime (crimes that can only be committed through the use of ICT devices, where the devices are both the tool for committing the crime and the target of the crime); or cyber–enabled crime (crimes that may be committed without ICT devices, like financial fraud, but are changed significantly by use of ICT in terms of scale and reach).[5] | ” |
United Nations[]
| “ | Two subcategories of cyber crime exist:
|
” |
United States[]
Cybercrime is
| “ | the use of the Internet and IT to steal valuable assets (e.g., money) from their rightful owners or otherwise to take actions that would be regarded as criminal if these actions were taken in person, and a breach of security is usually an important element of the crime.[7] | ” |
Overview[]
Conceptualizing cybercrime involves a number of key elements and questions that include where do the criminal acts exist in the real and digital worlds (and what technologies are involved in carrying out the crimes), why are malicious activities initiated, and who is involved in carrying out the malicious acts?
- One way of viewing cybercrimes is that they may be digital versions of traditional, real world offenses. They could be considered traditional, or "'real world," crimes if not for the incorporated element of the virtual world or cyberspace. In some instances, however, it may seem that law enforcement struggles to keep up with developments in the virtual world, which transform routine activities once driven by paper records in the real world. As a result, criminals are often prosecuted using laws intended to combat crimes in the real world.
- The distinction between cybercrime and other malicious acts in the virtual realm is the actor's motivation. Cyber criminals can exhibit a wide range of self interests, deriving profit, notoriety, and/or gratification from activities such as hacking, cyberstalking, and online child pornography. Without knowing the criminal intent or motivation, however, some activities of cyber criminals and other malicious actors may appear on the surface to be similar, causing confusion as to whether a particular action should be categorized as cybercrime or not. When referring to cybercrime incidents, terms such as cyber attack, cyber espionage, and cyber warfare are often loosely applied, and they may obscure the motives of the actors involved.
- Criminal attribution is a key delineating factor between cybercrime and other cyber threats. When investigating a given threat, law enforcement is challenged with tracing the action to its source and determining whether the actor is a criminal or whether the actor may be a terrorist or state actor posing a potentially greater national security threat. This is highlighted by examining the online collective known as Anonymous. Some refer to Anonymous as a group of online activists, others see the collective as a group of criminal actors, and still others have likened it to online insurgents.
Computers and other advanced technologies may be components of cybercrime through a variety of roles:
- in some cybercrimes, computers themselves — or data contained therein — are the victims or targets of crime;
- in other instances, computers or other digital technologies are used as tools for carrying out crimes (victimizing individuals, organizations, or government); and
- technological devices may serve as repositories for evidence of a cybercrime.
Computers significantly multiply the criminal's power and reach in committing such crimes.
Cybercrime also includes attacks against computers to deliberately disrupt processing, or may include espionage to make unauthorized copies of classified data. These attacks have such colorful names as:
Cybercrime techniques have characteristics that can vastly enhance the reach and impact of criminal activity, such as the following:
- Criminals do not need to be physically close to their victims to commit a crime.
- Technology allows criminal actions to easily cross multiple state and national borders.
- Cybercrime can be carried out automatically, at high speed, and by attacking a vast number of victims at the same time.
- Targets often do not realize they have been victimized until much later.
- Cybercriminals can more easily remain anonymous.
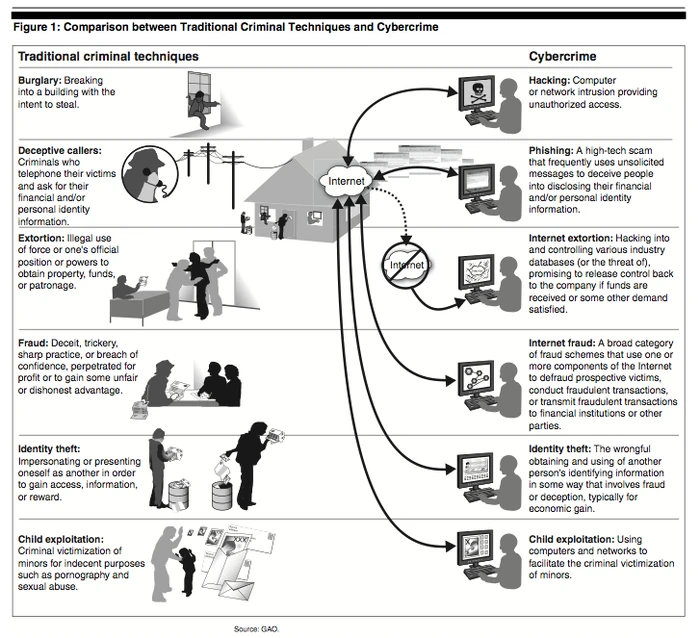
Figure 1 describes and compares cybercrime and traditional criminal techniques.
"There are direct and indirect costs to cybercrime victims including:
- damage to personal identity and reputation
- loss of business or employment opportunities
- impact on emotional and psychological wellbeing of individual victims.
The actual costs of cybercrime at the systemic level encompass the:
- financial losses from fraud
- costs of immediate responses
- system remediation costs
- flow-on costs to government support programs that assist cybercrime victims.
The complexity, sophistication and impact of cybercrime evolves as technology evolves, making it difficult to track the technological advancements of cyber criminals. Furthermore, the complexity and sophistication of malware used for cybercrime now rivals the capabilities of some state-sponsored adversaries."[8]
Cyberterrorism[]
If a terrorist group were to launch a cyberattack to cause harm, such an act also fits within the definition of a cybercrime. The primary difference between a cyberattack to commit a crime or to commit terror is found in the intent of the attacker, and it is possible for actions under both labels to overlap.
Often it is very difficult to determine if a cyberattack or intrusion is the work of a terrorist organization with the objective of doing harm, or a cybercriminal who wishes to steal information for purposes of monetary gain. Just as terrorists and violent extremists often rely on exploiting vulnerabilities of targets seen as soft and easy to access to support possible future cyberattacks, cybercriminals exploit these same vulnerabilities to gain access to information that may lead to monetary gain.
The proportion of cybercrime that can be directly or indirectly attributed to terrorists is difficult to determine. However, linkages do exist between terrorist groups and criminals that allow terror networks to expand internationally through leveraging the computer resources, money laundering activities, or transit routes operated by criminals.
Implementation of a stronger policy for domestic physical security has reduced the risk to some targets that may have previously been vulnerable to physical attacks. Also, it is suggested by numerous experts that terrorists may be enhancing their computer skills or forming alliances with cybercriminals that possess a high-level of telecommunications expertise. In addition, continuing publicity about Internet security vulnerabilities may encourage terrorists' interest in attempting a possible computer network attack, or cyberattack, against U.S. critical infrastructure.
Extent of cybercrime activities[]
Cybercrime is a threat to worldwide economic and security interests. Various studies and expert opinion estimate the direct economic impact from cybercrime to be in the billions of dollars annually. One estimate has placed the annual cost of cybercrime to adults in 24 countries across the globe at $388 billion.[9]
Law enforcement activities[]
Numerous public and private entities (federal agencies, state and local law enforcement, industry, and academia) have individual and collaborative responsibilities to protect against, detect, investigate, and prosecute cybercrime. The Departments of Justice (DOJ), Homeland Security (DHS), and Defense (DOD), and the Federal Trade Commission (FTC) have prominent roles in addressing cybercrime within the federal government.
DOJ's FBI and DHS's U.S. Secret Service (Secret Service) are key federal organizations with responsibility for investigating cybercrime. The FBI Cyber Division focuses on "high-level intrusions by state-sponsored hackers and global cyber syndicates, and the most prolific botnets."[10]
State and local law enforcement organizations also have key responsibilities in addressing cybercrime. Private entities — Internet service providers, security vendors, software developers, and computer forensics vendors — focus on developing and implementing technology systems to protect against computer intrusions, Internet fraud, and spam and, if a crime does occur, detecting it and gathering evidence for an investigation.
In addition, numerous partnerships have been established between public sector entities, between public and private sector entities, and internationally to address various aspects of cybercrime. For example, the Cyber Initiative and Resource Fusion Unit is a partnership established among federal law enforcement, academia, and industry to analyze cybercrime and determine its origin and how to fight it.
Challenges to addressing cybercrime[]
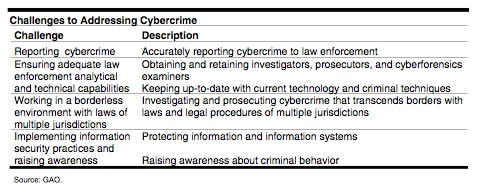
Entities face a number of key challenges in addressing cybercrime, including reporting cybercrime and ensuring that there are adequate analytical capabilities to support law enforcement (see table below). While public and private entities, partnerships, and tasks forces have initiated efforts to address these challenges, federal agencies can take additional action to help ensure adequate law enforcement capabilities.
International law[]
Cybercrime laws vary across the international community. Australia enacted its Cybercrime Act 2001 to address this type of crime in a manner similar to the U.S. Computer Fraud and Abuse Act. In addition, Japan enacted the Unauthorized Computer Access Law of 1999 to cover certain basic areas similar to those addressed by the U.S. federal cybercrime legislation.
Council of Europe Convention on Cybercrime[]
Because political or natural boundaries are not an obstacle to conducting cybercrime, international agreements are essential to fighting cybercrime.
On November 23, 2001, the United States and 29 other countries signed the Council of Europe's Convention on Cybercrime as a multilateral instrument to address the problems posed by criminal activity on computer networks.
The Convention on Cybercrime distinguishes between four different types of offences:
- Offences against the confidentiality, integrity and availability of computer data and systems;[11]
- Computer-related offences;[12]
- Content-related offences;[13] and
- Copyright-related offences.[14]
Nations supporting this Convention agree to have criminal laws within their own nation to address cybercrime, such as hacking, spreading viruses or worms, and similar unauthorized access to, interference with, or damage to computer systems. It also enables international cooperation in combating crimes such as child sexual exploitation, organized crime, and terrorism through provisions to obtain and share electronic evidence. The U.S. Senate ratified this convention in August 2006.
References[]
- ↑ National Plan to Combat Cybercrime, at 4.
- ↑ Towards a general policy on the fight against cyber crime §1.1.
- ↑ Art. 1.1, Draft International Convention to Enhance Protection from Cyber Crime and Terrorism (CISAC).
- ↑ Cybercrime: Public and Private Entities Face Challenges in Addressing Cyber Threats, at 1.
- ↑ National Cyber Security Strategy 2016 to 2021, Glossary, Annex 2, at 14.
- ↑ Crimes Related to Computer Networks: Background Paper for the Workshop on Crimes Related to the Computer Network, at 5 ¶18.
- ↑ At the Nexus of Cybersecurity and Public Policy: Some Basic Concepts and Issues, at 13.
- ↑ ACSC 2015 Threat Report, at 9.
- ↑ Norton, Symantec Corporation, "Norton Study Calculates Cost of Global Cybercrime: $114 Billion Annually" (Sept. 7, 2011) (full-text). See also Norton, Symantec Corporation, Cybercrime Report 2011 (full-text). This $388 billion includes $114 billion in direct financial losses (amount stolen by cybercriminals and amount spent on resolving the cyber threats) as well as more than $274 billion in victim valued time lost to cybercrime.
- ↑ Statement of former FBI Director James B. Comey before the U.S. Congress, House Committee on the Judiciary, Oversight of the Federal Bureau of Investigation, 114th Cong., 2nd Sess. (Sept. 28, 2016).
- ↑ Convention on Cybercrime, Art. 2 (Illegal access), Art. 3 (Illegal interception), Art. 4 (Data interference), Art. 5 (System interference), Art. 6 (Misuse of devices).
- ↑ Convention on Cybercrime,Art. 7 (Computer-related forgery), Art. 8 (Computer-related fraud).
- ↑ Convention on Cybercrime, Art. 9 (Offences related to child pornography).
- ↑ Convention on Cybercrime, Art. 10 (Offences related to infringements of copyright and related rights).
See also[]
- Between line entry
- Computer crime
- Computer Crime and Security Survey
- Computer Crime Enforcement Act
- Cyber Crimes Center
- Cyber Crimes Section
- Cybercrime Institute
- Cybercrime Operations
- Cyber Crime-A Growing Challenge for Governments
- Cybercrime: An Overview of the Federal Computer Fraud and Abuse Statute and Related Federal Criminal Laws
- Cybercrime: Conceptual Issues for Congress and U.S. Law Enforcement
- Cybercrime: Public and Private Entities Face Challenges in Addressing Cyber Threats
- Cybercrime: The Council of Europe Convention
- Internet-enabled crime
- Internet-facilitated crime
- Pure cybercrime
- Technology-enabled crime
- U.S. Department of Justice, Computer Crime and Intellectual Property Section
Sources[]
- Cybercrime: Conceptual Issues for Congress and U.S. Law Enforcement, Summary.
- Cybercrime: Public and Private Entities Face Challenges in Addressing Cyber Threats.
External resources[]
- Council of Europe, Legislation-Country Profiles.
- Cybercrime laws from around the world.
- Darío N. Rolón, "Vigilancia informática y responsabildiad penal de los proveedores de internet" (Colombia 2013) (full-text).